
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur.
Block quote
Ordered list
Unordered list
Bold text
Emphasis
Superscript
Subscript
With the recent release of Meraki Access Manager & Cloud PKI, cloud-only organizations have additional options on securing their Wi-Fi. With support for certificate-based 802.1X authentication using EAP-TLS and Entra ID-based device lookup, this combo eliminates the friction of passwords and raises the bar on endpoint trust.
The only catch? The Meraki Access Manager is still in early access, and no general availability date has been announced. For IT teams eager to get ahead of the curve, that means piecing together documentation, release notes, and forums to make it all work.
To save you the time and trial-and-error, our cofounder Gary Greenberg has provided a guide of a validated working configuration that walks you through the full setup—from enabling Access Manager to configuring Intune Cloud PKI for seamless EAP-TLS authentication.
Ready to get your hands dirty? Let’s dive in.

As enterprise IT teams shift toward zero-trust networking, securing wireless authentication becomes a critical component of the infrastructure. This guide presents a modern, cloud-native approach using Cisco Meraki Access Manager and Microsoft Intune Cloud PKI to implement certificate-based 802.1X EAP-TLS authentication.
The result: stronger security, simplified deployment, and no need for on-prem RADIUS or on-prem PKI infrastructure. While this article focuses on wireless 802.1X authentication, Meraki Access Manager also supports other features like wired 802.1X network access control—a topic we will explore in a follow-up guide (Part 2).
Hypershift has successfully tested and implemented this configuration and can help your organization do the same.
Enterprise wireless authentication is evolving—and organizations using Cisco Meraki and Microsoft Intune now have a sleek, secure path forward. This article explains how to pair Meraki Access Manager (currently in Early Access) with Microsoft Intune Cloud PKI to implement EAP-TLS wireless authentication, eliminating on-prem PKI/RADIUS infrastructure and delivering a seamless certificate-based solution.
Traditional Wi-Fi deployments rely on a shared password, exposing networks to serious risks. Once that password is compromised—whether by an ex-employee or a malicious actor—your entire network is vulnerable. Changing the PSK disrupts all users and devices.
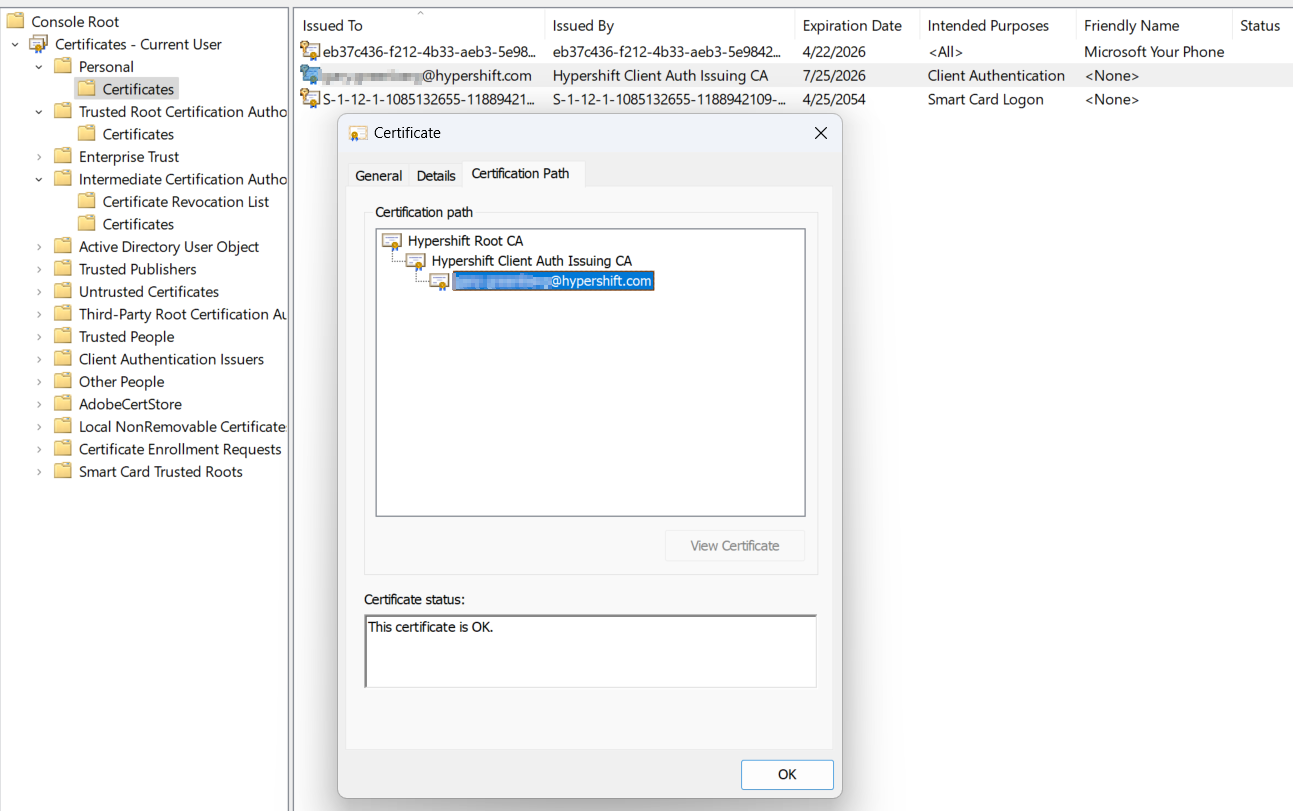
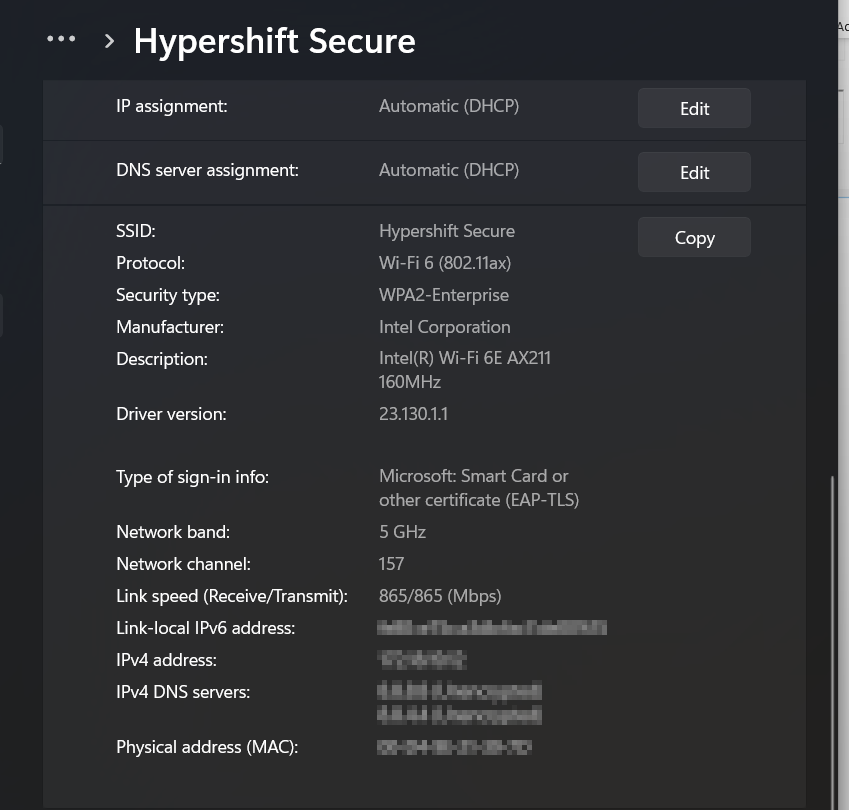
Enterprise wireless authentication with EAP-TLS solves this by using digital certificates for per-device or per-user authentication. Only devices that are managed, compliant, and have valid certificates can connect, significantly reducing attack surface and administrative overhead.
Until now, Meraki relied on external RADIUS servers (typically Microsoft NPS or Cisco ISE) for 802.1X authentication. But with Access Manager, Meraki now offers a cloud-native RADIUS service built directly into the dashboard—no hardware to install, no on-prem server to maintain.
Currently in Early Access, Access Manager lets Meraki-managed environments enable 802.1X authentication from the cloud, optionally integrating with Microsoft Entra ID for identity lookup control. At the time of writing the public beta Meraki Access Manager is free to use, with pricing and licensing details expected to be announced when it reaches general availability.
Key Features:
Many small to midsize organizations have moved away from on-prem PKI due to complexity and maintenance costs. With Intune Cloud PKI, Microsoft offers a managed certificate authority that issues client authentication certificates via SCEP or PKCS—ideal for Intune managed devices.
Cloud PKI removes the need to run your own CA and simplifies certificate deployment:
Cloud PKI pricing at the time of writing:

Tip: While easy to deploy, large enterprises should be aware that costs can scale quickly. For example, 30,000 users could equate to $720,000 per year if using the standalone Cloud PKI license.
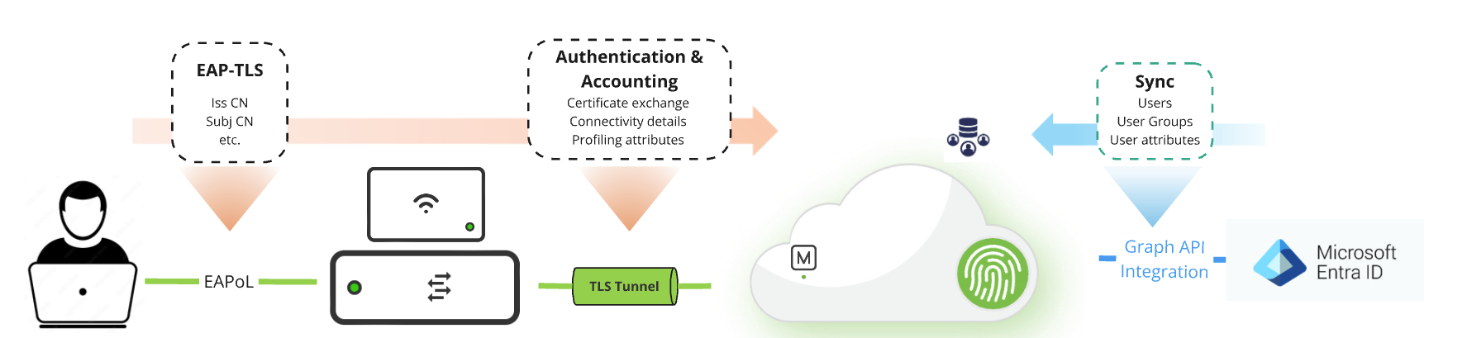
1. A client attempts to connect to a Meraki SSID.
2. The MR access point forwards the EAP-TLS request to Meraki Cloud via Access Manager.
3. The client presents its Intune-issued certificate.
4. Access Manager validates the certificate and optionally performs an Entra ID lookup.
5. Access rules (VLAN, group policies, etc.) are applied based on certificate and identity.
6. Network access is granted.
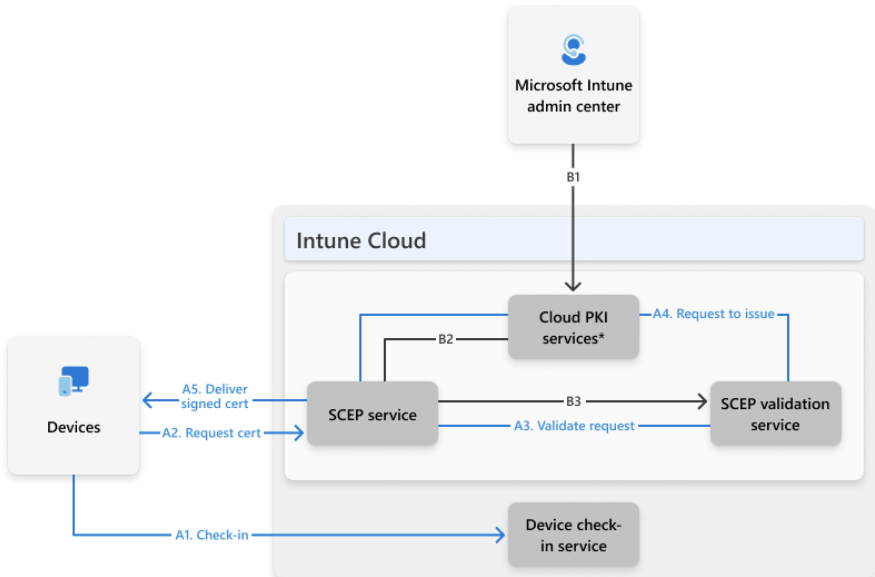
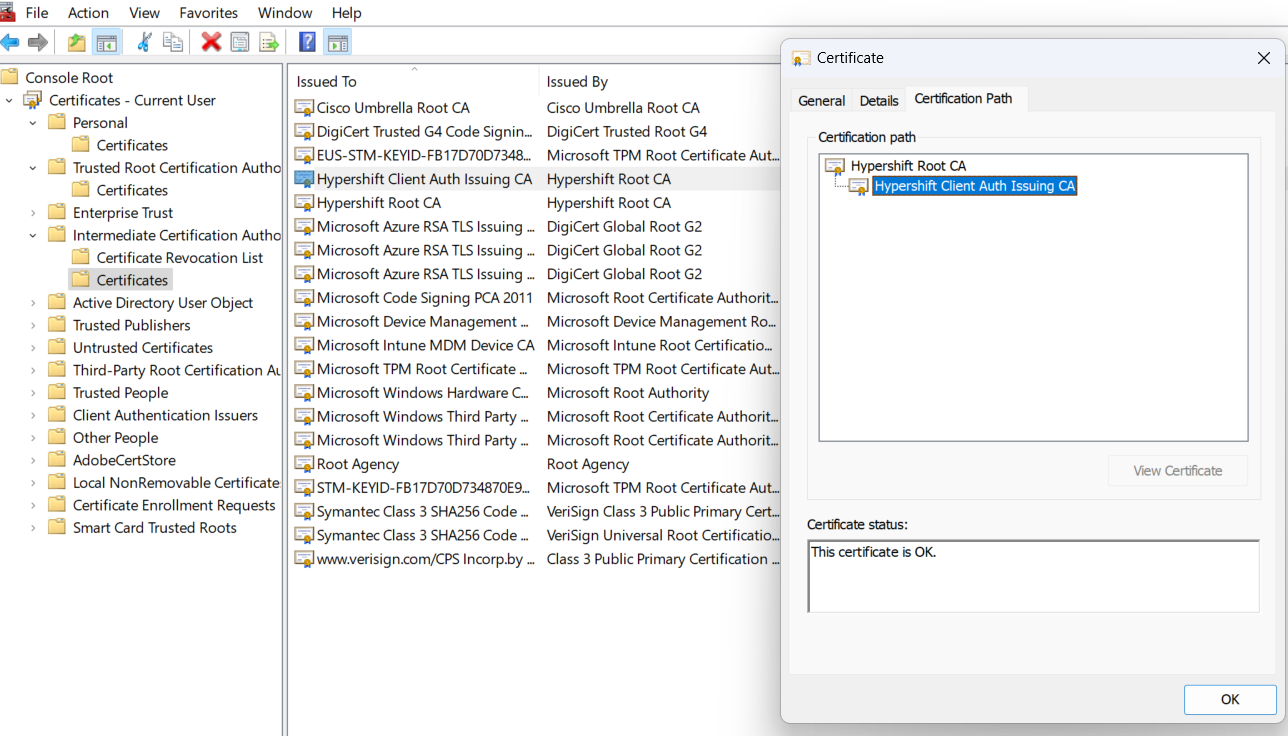
Cloud PKI works by securely issuing certificates to devices using the Simple Certificate Enrollment Protocol (SCEP). The process begins with an admin provisioning Root and Issuing CAs through the Intune Admin Center. When a device checks in (A1), it initiates a certificate request (A2) to the SCEP service.
From there:
This flow ensures:
With no need for an on-prem CA or NDES connector, this architecture significantly simplifies secure certificate distribution while maintaining full control through Intune policy.

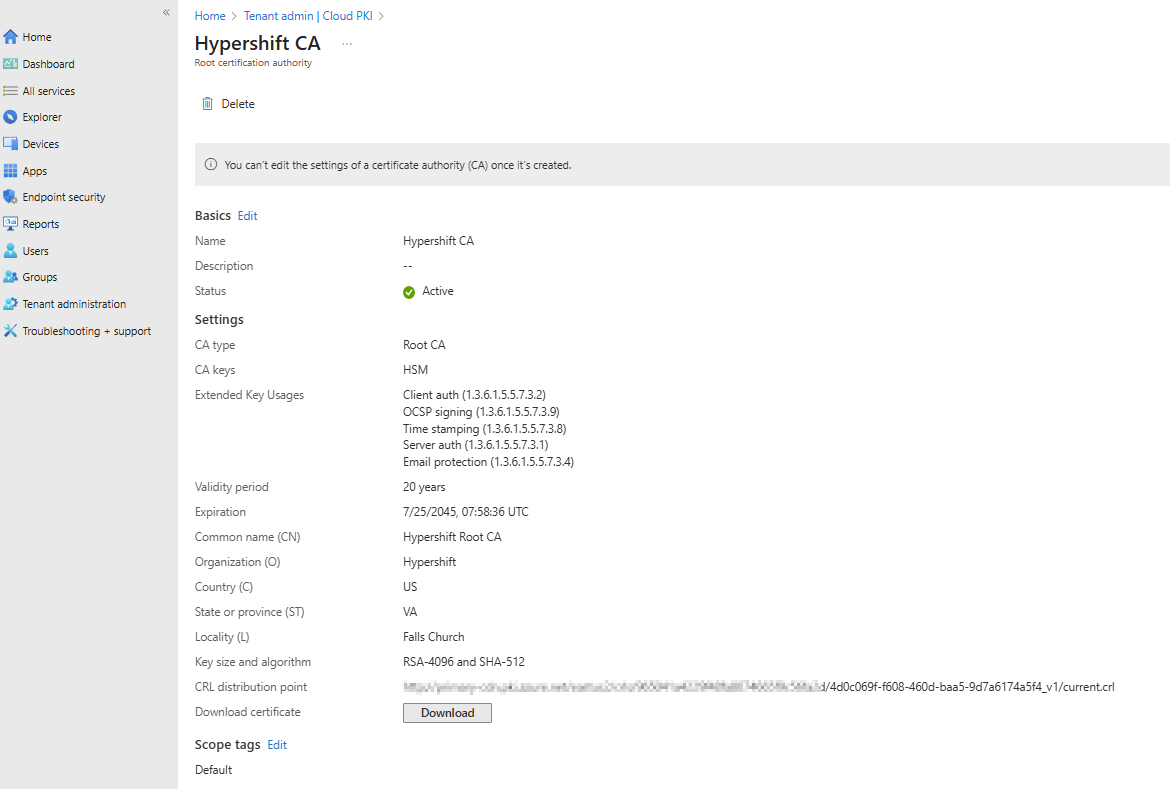
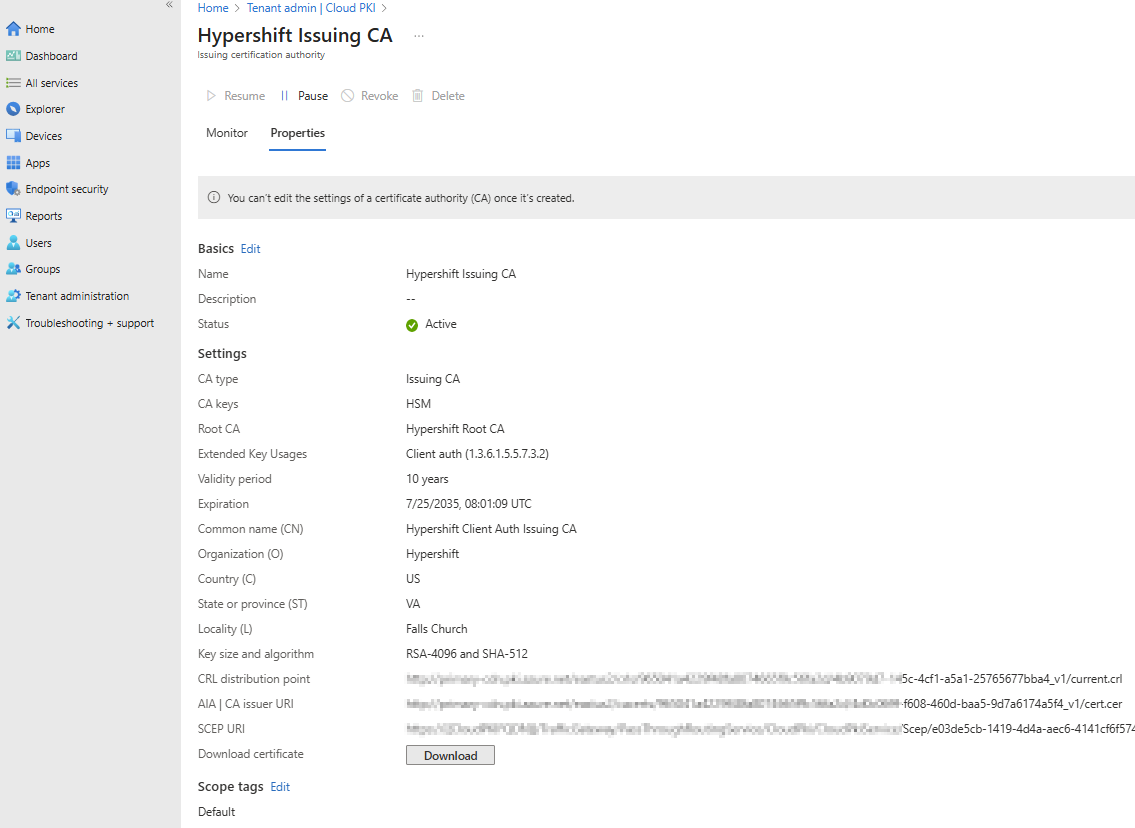
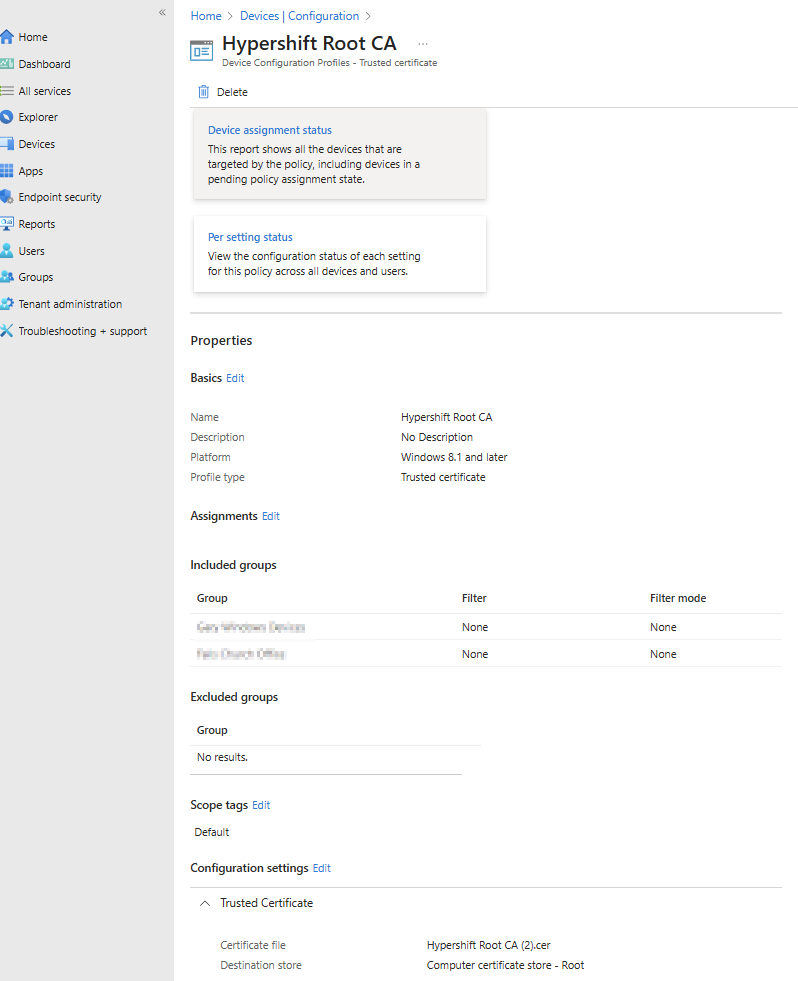
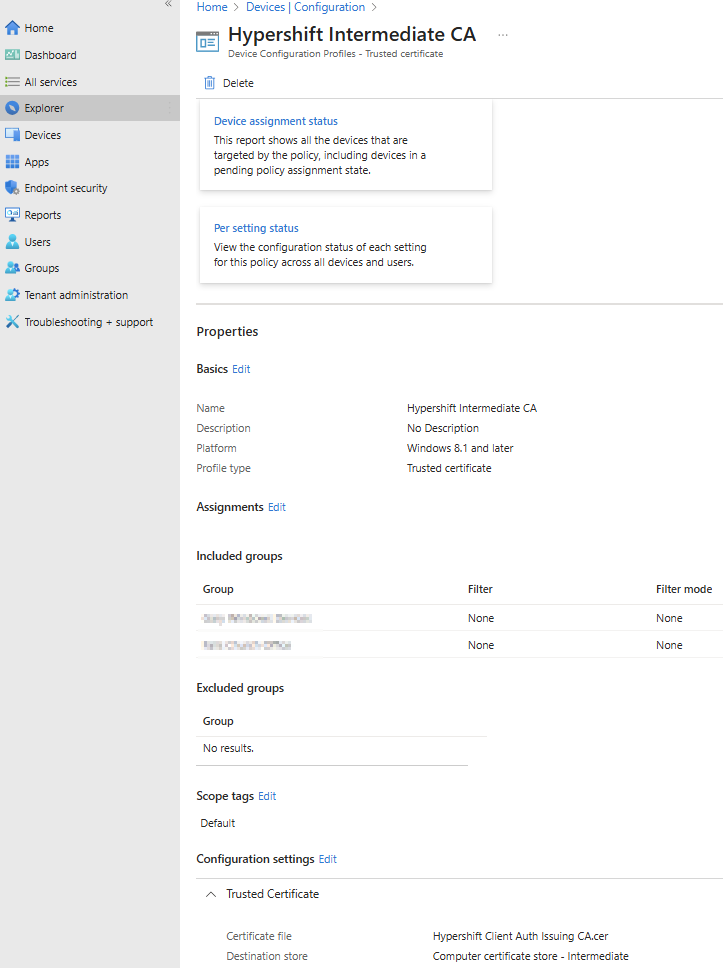
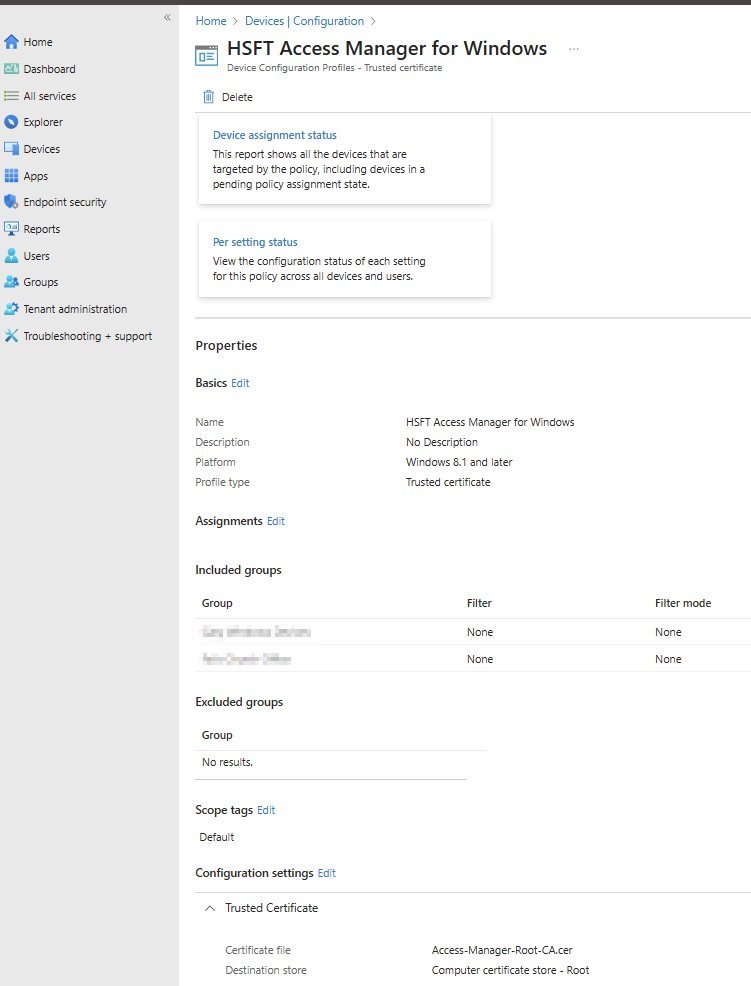
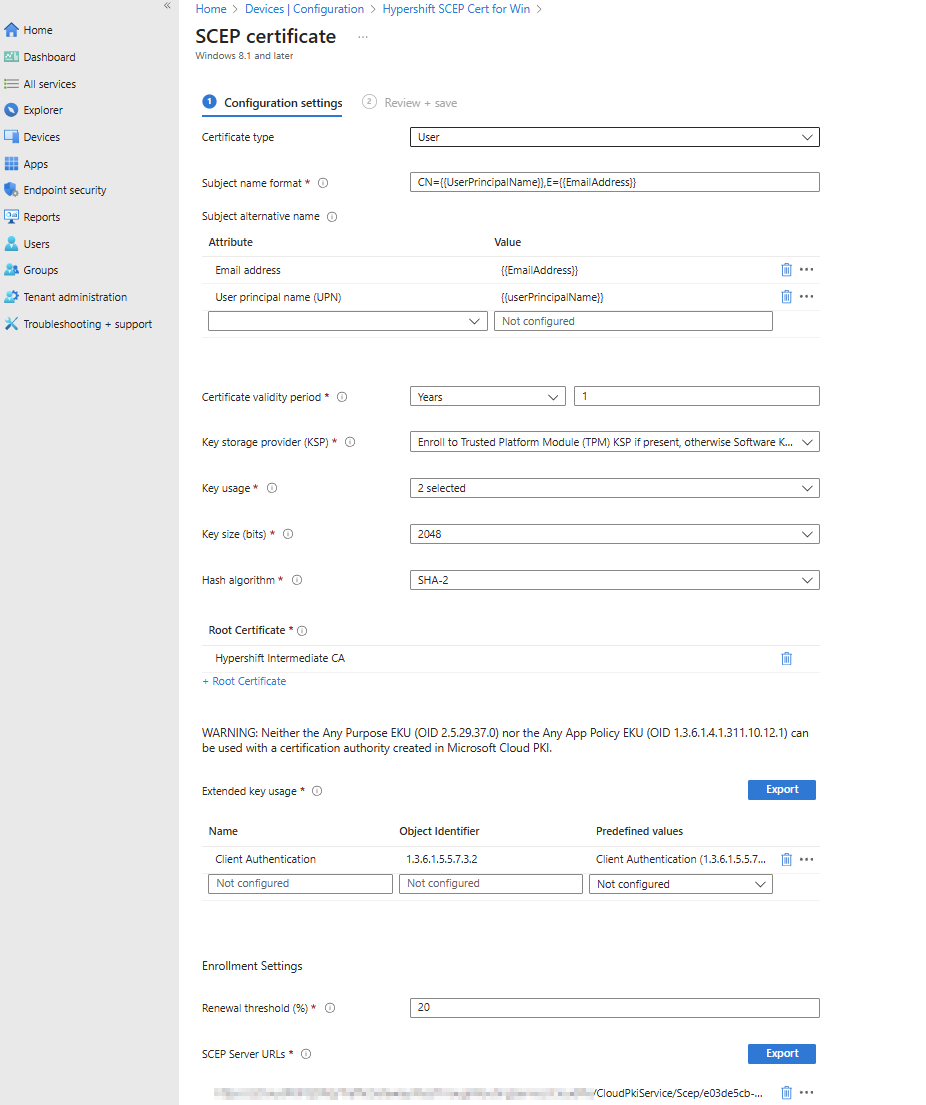
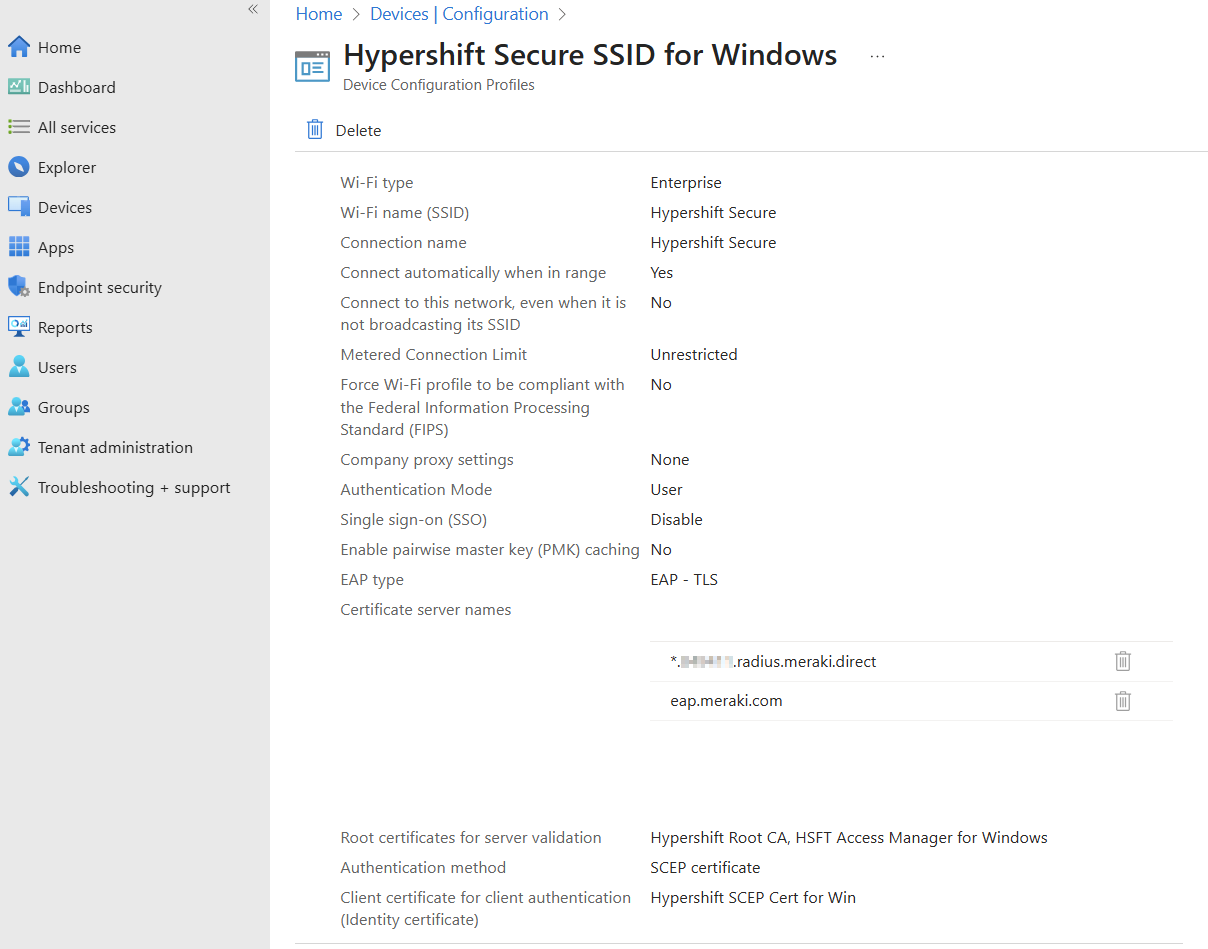
Tip: Add certificate server names for Access Manager certificates to prevent the trust dialog box from prompting when connecting to the SSID. See the Intune Wi-Fi profile section for details.
* For detailed instructions on client configuration, follow this link here.
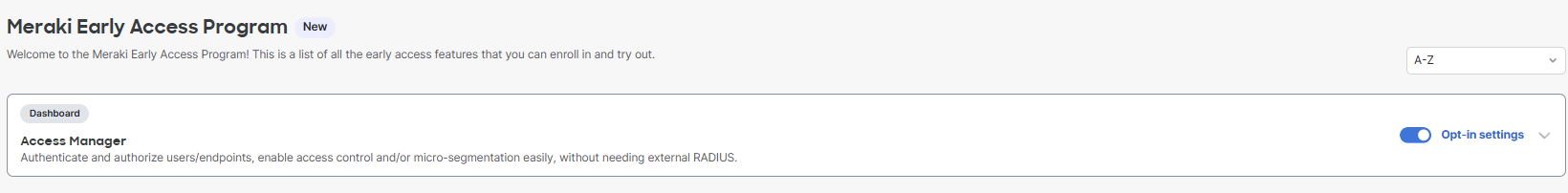
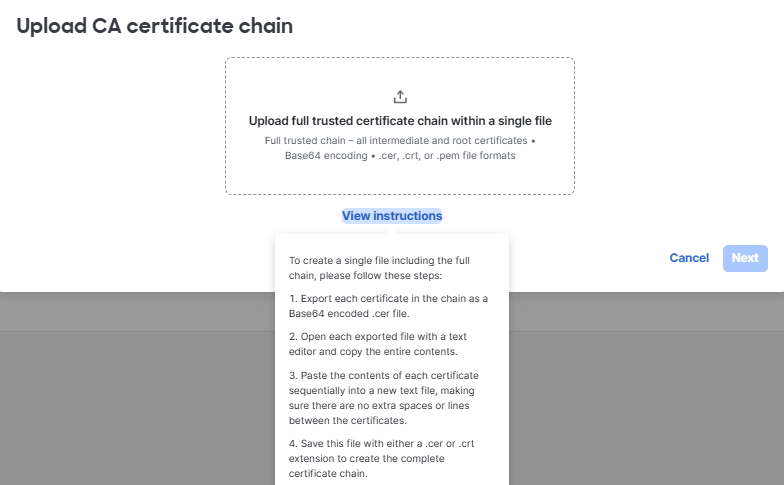
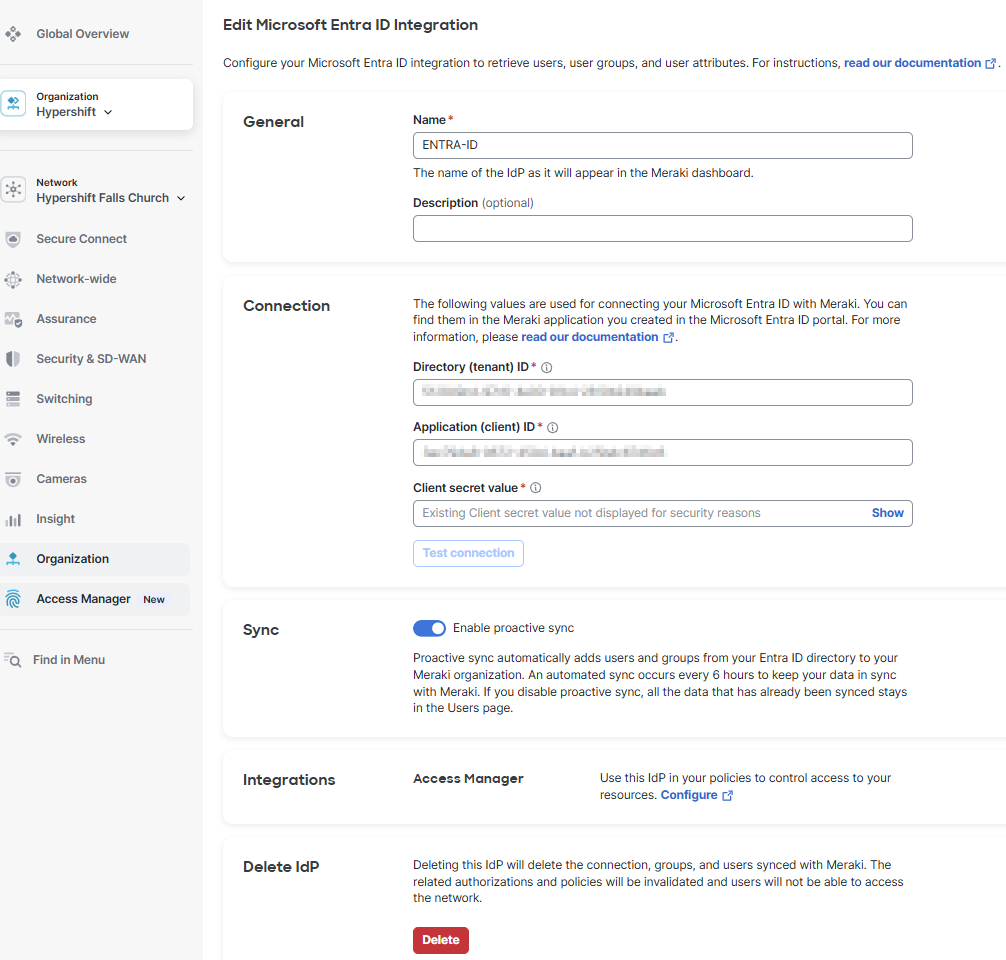
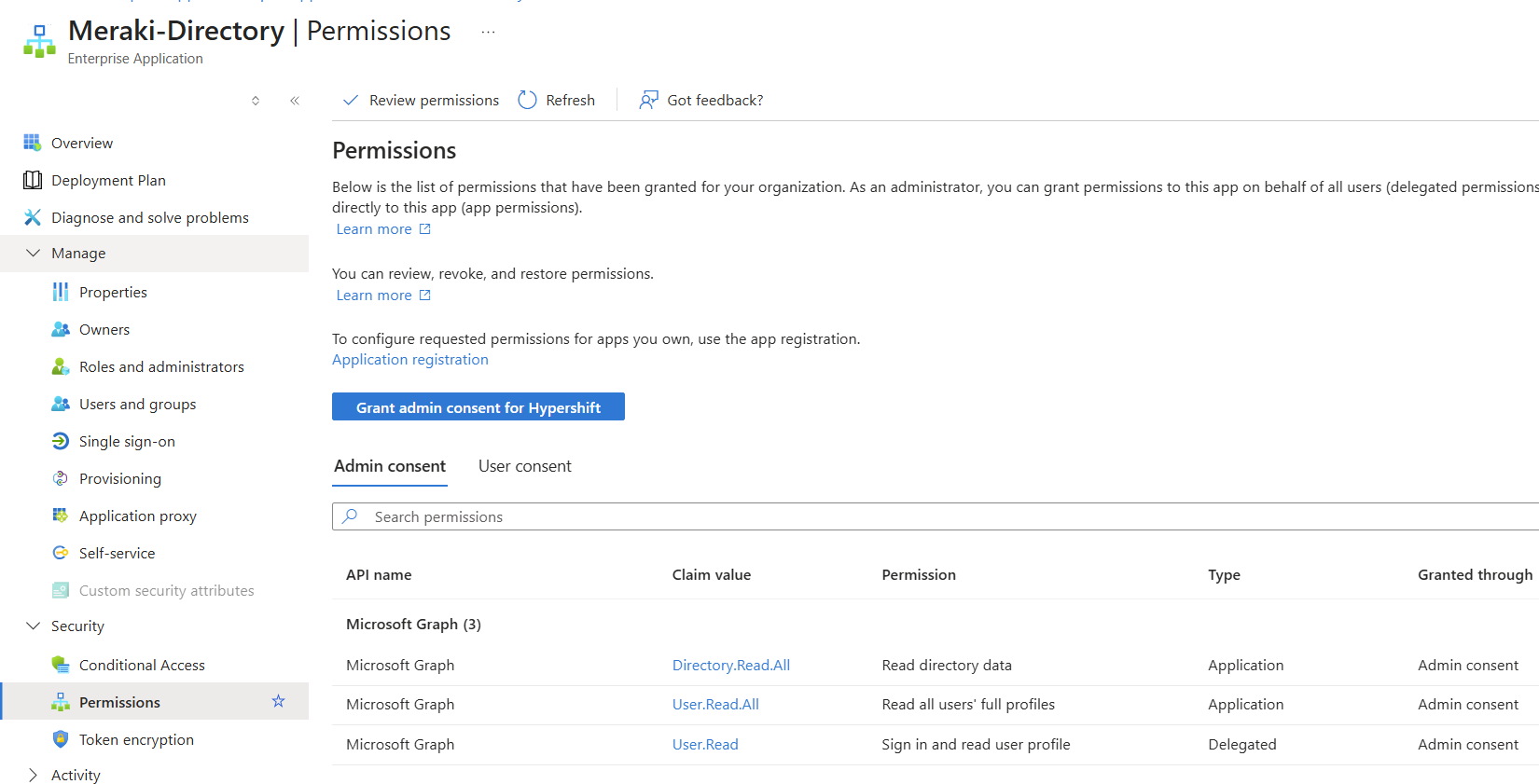
For detailed instructions to integrate Entra ID w/ Meraki, follow this link here.
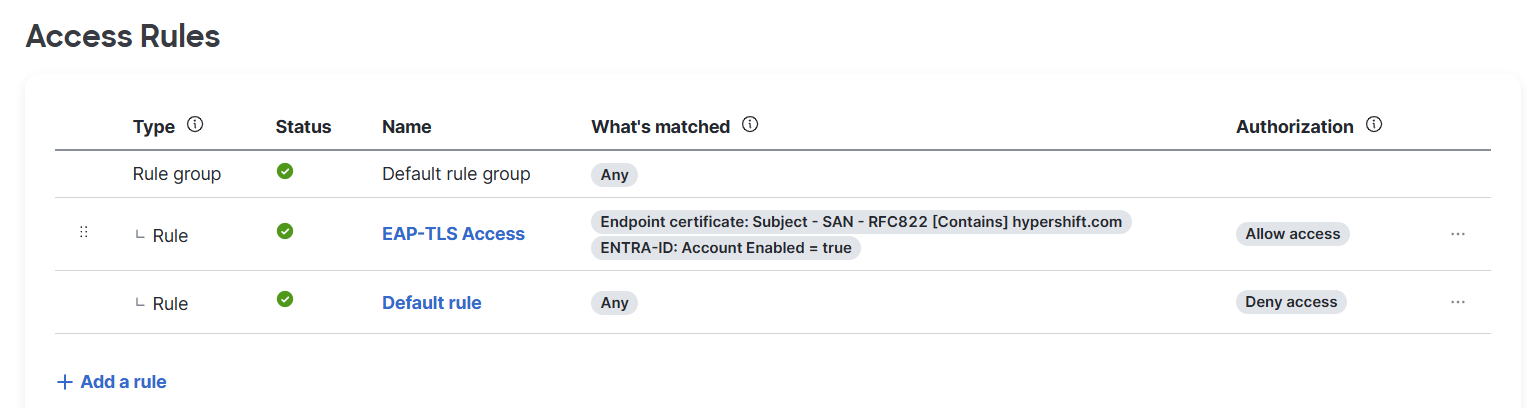
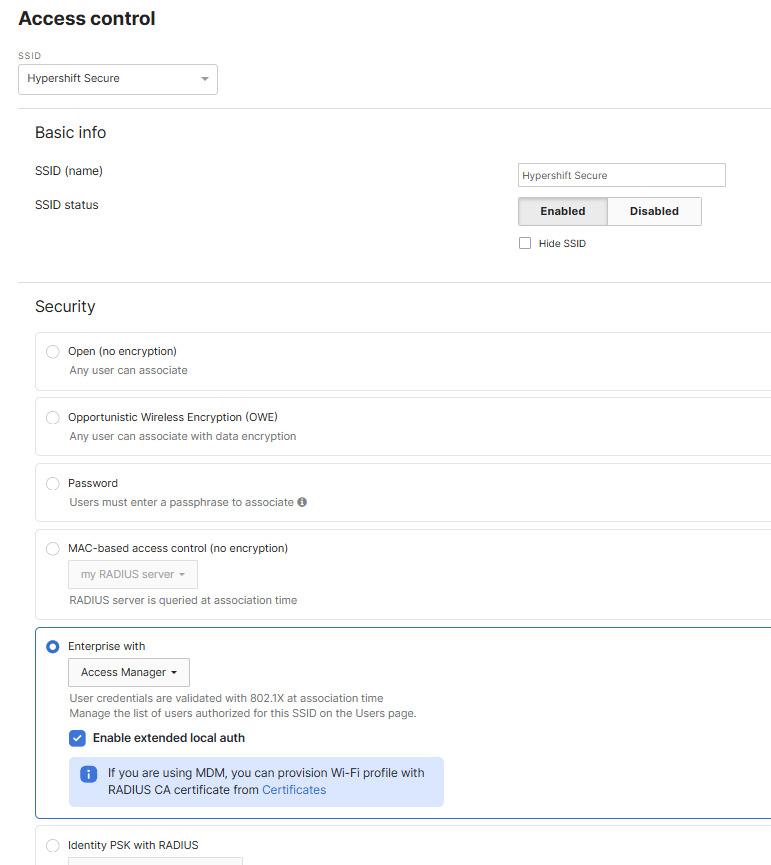
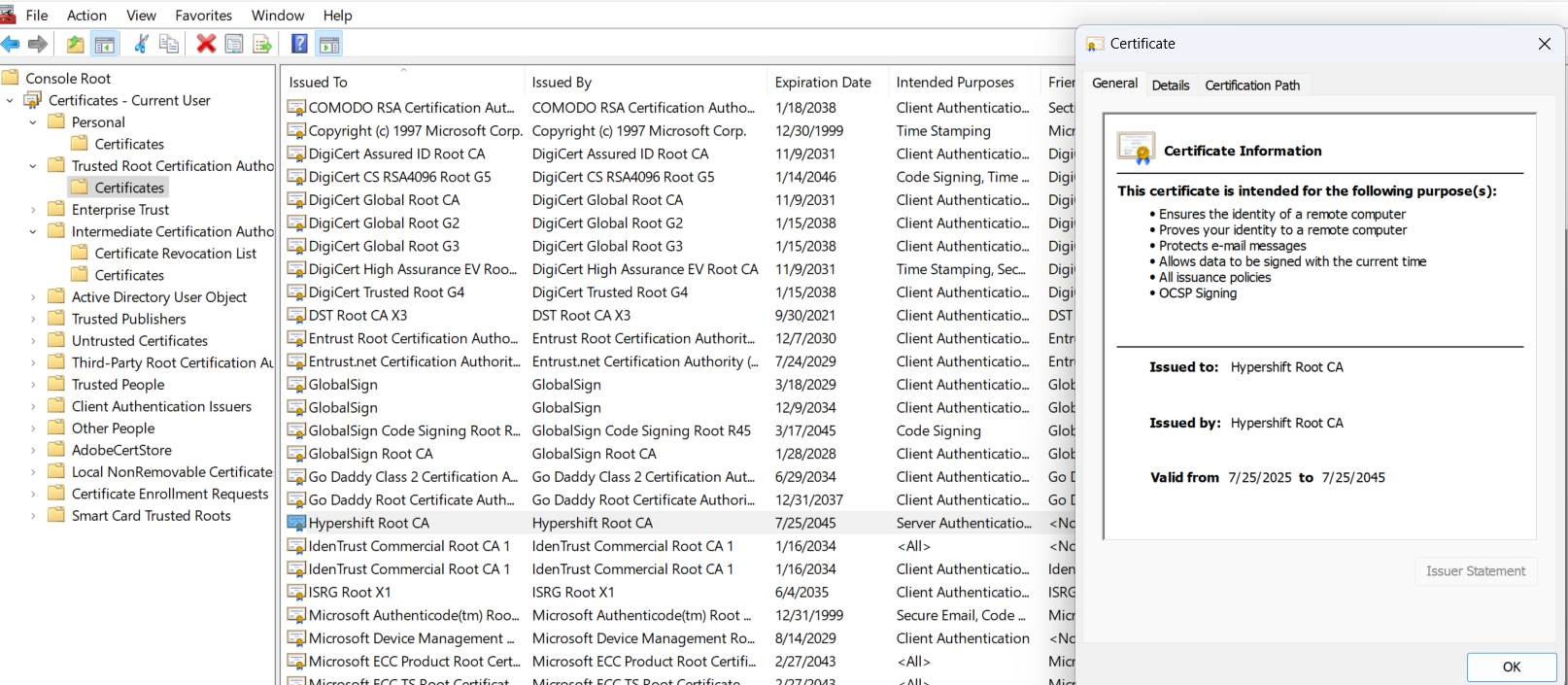
Hypershift specializes in helping IT teams adopt cloud-first, secure networking solutions. We've designed and tested this Meraki + Intune PKI integration and can guide your team from design to deployment.
Our Services Include:
Get in touch: https://hypershift.com/contact
Enterprise wireless security doesn't have to be complex. With Meraki Access Manager and Microsoft Intune Cloud PKI, you can deploy a scalable, cloud-native solution that improves security and simplifies management. Ready to modernize your network?
Hypershift is here to help.